Zero trust architecture is a security philosophy that focuses on reducing the points of access and exposure to mitigate risk. By implementing zero trust, organizations can gain better visibility over their IT environment, enabling them to secure resources across vast networks.
Using a managed security service provider (MSSP) or other cybersecurity services solution provider to design and deploy your zero trust architecture can be a great way to reduce friction and time-to-market. These experts have the experience, knowledge, and resources to help you maximize the security of your network.
Importance of implementing Zero Trust for cybersecurity
Zero trust architecture is a key part of robust cybersecurity. By relying on identity-driven access control, this approach can help protect your digital assets and enhance network security. It also helps organizations meet compliance requirements and protect their data from external threats.
The benefits of zero trust architecture don’t end there. This type of security framework provides enhanced visibility, better user authentication, improved auditability and less operational overhead.
Layering Security with Zero Trust Architecture
Zero trust architecture is focused on segmenting access to sensitive assets and resources. To do this, you must first determine the most critical points of your network and organize them into separate zones. The idea is to minimize risk by preventing threats from propagating across multiple zones.
You can then use various security measures to protect each zone, such as firewalls and other network access control (NAC) systems. Finally, you must ensure that all users have the necessary authentication credentials to access the resources in each zone. This layered approach ensures that only authorized personnel will be able to access sensitive data or assets.
Zero Trust architecture and its core principles
The core principles of zero trust architecture are authentication, authorization, auditability, and accountability.
Authentication requires that all users have the correct credentials to access resources.
Authorization ensures that only authorized personnel can access the resources.
Auditability is important for tracking who has accessed each resource.
Accountability provides a way to determine who should be held liable in the event of a breach.
By following these core principles and implementing the right security measures, organizations can ensure that their assets are securely protected from external threats.
Key Challenges in Implementing Zero Trust
Knowing how to implement zero-trust security requires an understanding of the most common obstacles you may encounter. These include complex infrastructures, cost, effort, and the need for flexible software solutions.
Organizations must also be aware of the potential risks associated with zero trust architecture. These include a lack of visibility into user activities, compliance issues due to data transfer restrictions, and poor configuration management if not done properly.
1: Legacy Systems and Infrastructure
One of the most common challenges organizations face when implementing zero-trust architecture is their legacy infrastructure. Many organizations have older systems that may not be compatible with modern security measures. To solve this issue, they should consider migrating to more secure and up-to-date solutions that are better equipped to handle today’s threats.
2: User Adoption and Change Management
Secondly, another challenge organizations face is getting users to adopt the new security measures. This can be especially difficult if your organization is used to relying on outdated systems or practices. To ensure user adoption, it’s important to provide training and resources that help them understand how zero-trust architecture works and how they can best take advantage of its benefits.
3: Policy Enforcement and Access Control
One of the biggest challenges organizations face is ensuring that their policies are enforced throughout the organization. This requires an effective access control system and a rigorous enforcement policy. To do this, organizations should consider using tools such as identity-based authentication and authorization.
4: Continuous Monitoring and Threat Detection
Lastly, organizations should be aware of the potential risks associated with zero-trust architecture. Continuous monitoring and threat detection are essential for staying ahead of any threats that might threaten your network’s security. To do this, you should invest in advanced security tools such as SIEM (Security Information and Event Management) systems to monitor user activity on your network.
Proven Solutions for Zero Trust Implementation
Organizations that are serious about implementing zero-trust architecture should consider using proven solutions. These solutions can help organizations reduce the risks associated with zero trust by providing them with advanced security tools and services.
These solutions include:
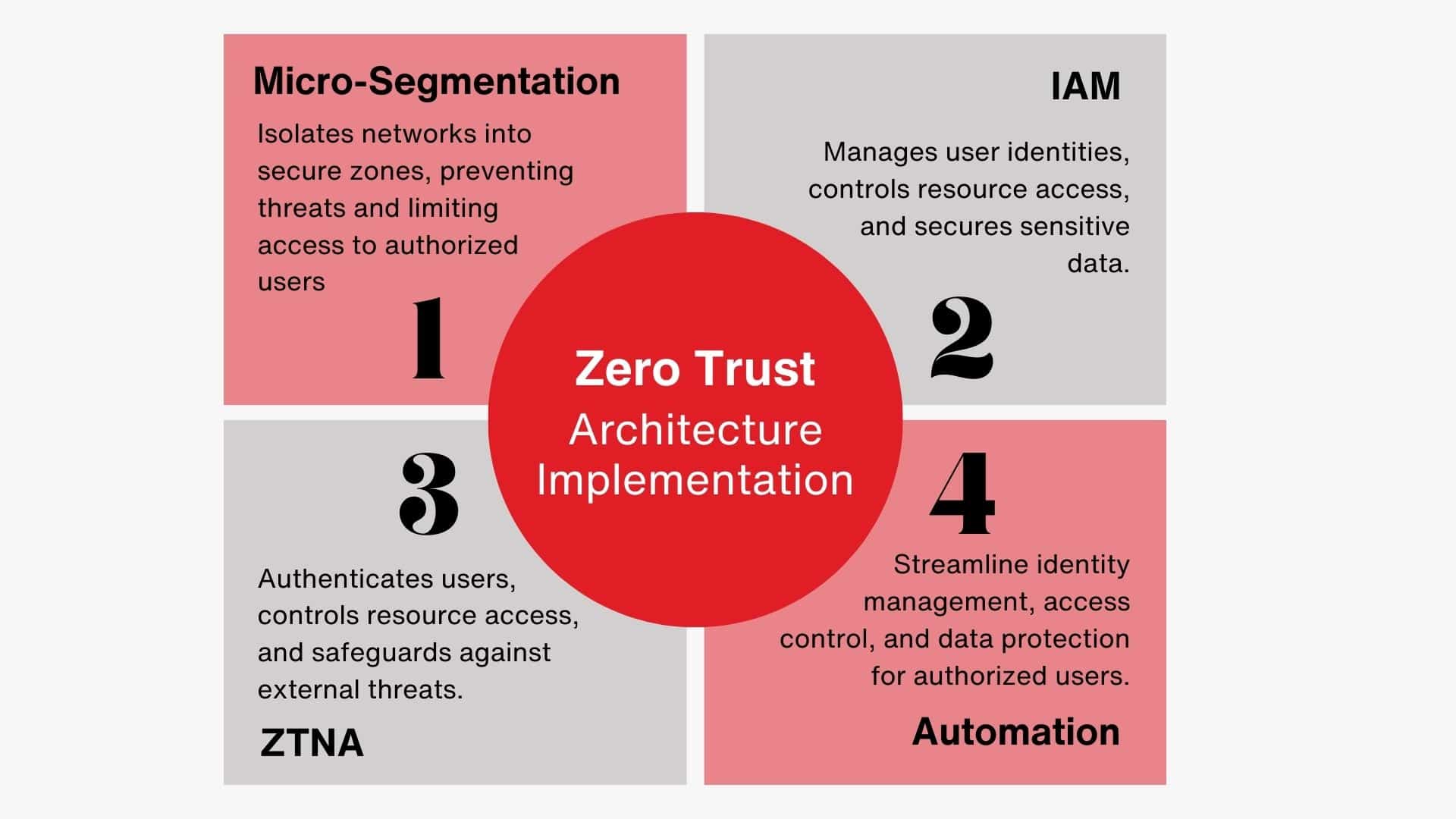
1: Micro-Segmentation
Micro-segmentation is an essential part of zero-trust architecture. This technique involves splitting large networks into smaller, more secure zones that are isolated from each other. By segmenting your network in this way, you can prevent threats from propagating across multiple zones and ensure only authorized personnel have access to sensitive assets.
2: Identity and Access Management (IAM)
Secondly, Identity and access management (IAM) is a key part of zero trust architecture. This solution helps organizations manage user identities, control access to resources, and ensure that only authorized users have access to sensitive data or assets.
3: Zero Trust Network Access (ZTNA)
Zero trust network access (ZTNA) is a security solution that combines identity and access management with micro-segmentation. This solution helps organizations authenticate users, control who has access to resources, and protect their networks from external threats.
4: Automation and Orchestration
Finally, automation and orchestration are essential tools for organizations looking to implement zero trust architecture. These solutions help streamline the process of managing user identities, controlling access to resources, and ensuring that only authorized personnel have access to sensitive data or assets.
Conclusion
Zero trust architecture is a critical component of modern cybersecurity. Organizations can ensure the secure protection of their sensitive assets from external threats by actively adhering to the core principles of authentication, authorization, auditability, and accountability. However, implementing zero-trust security presents several challenges, such as dealing with legacy infrastructure, addressing issues related to user adoption and change management, struggling with policy enforcement and access control, and maintaining continuous monitoring and threat detection.
Organizations that are serious about implementing zero-trust architecture should consider using proven solutions. These solutions can help organizations reduce the risks associated with zero trust by providing them with advanced security tools and services.

