Penetration testing, commonly known as pentest, is a type of cyber attack simulation intended to test computer systems or networks and assess their security. A security professional known as a penetration tester uses various strategies and exploits vulnerabilities within them to gain unauthorized entry and access.
Penetration Testing: Types of PenTest
SCADA penetration testing specializes in testing Supervisory Control and Data Acquisition (SCADA) systems used to manage critical infrastructure such as power plants, water treatment plants, or transportation systems. SCADA systems often present large attack surfaces, making them attractive targets for attackers; pen-testing using SCADA technologies can assist organizations in identifying and resolving security vulnerabilities within SCADA systems.
Wireless penetration testing (WPT) is a form of security auditing that specifically tests wireless networks. Wireless networks are often found in homes, businesses, and organizations and are susceptible to eavesdropping, man-in-the-middle attacks, and denial-of-service attacks. WPT can assist organizations by helping identify and resolve security vulnerabilities on their wireless networks.
Cloud penetration testing is a form of pen testing that specifically examines cloud-based systems and applications. Organizations of all sizes utilize such services, making them vulnerable to data breaches, denial-of-service attacks, and account hijacking attacks. Cloud penetration testing helps organizations identify and address security vulnerabilities within these cloud platforms and applications.
Database penetration testing is a type of pen-testing that specifically examines databases. Databases store sensitive customer information, financial details, and intellectual property. As a result, they are vulnerable to attacks such as SQL injection, cross-site scripting, and denial-of-service attacks; database penetration testing can assist organizations in identifying and remedying security vulnerabilities within their databases.
IoT penetration testing is a type of pen-testing explicitly designed to evaluate Internet of Things (IoT) devices. These connected devices collect and transmit data over the internet. IoT devices are vulnerable to denial-of-service attacks, data breaches, and malware attacks. Penetration testing helps organizations detect and fix vulnerabilities within these devices.
Social engineering penetration testing is a form of pen-testing that specializes in social engineering attacks. Such attacks use subtle psychological manipulation techniques to convince individuals to reveal sensitive data or take harmful actions against an organization. Social engineering pen-testing helps organizations detect and remedy security vulnerabilities susceptible to social engineering attacks.
OT penetration testing (also referred to as operational technology (OT) pen-testing) is a type of pen-testing explicitly designed to assess active technology (OT) systems used in industrial processes like power plants, water treatment plants, and transportation networks. As these OT systems often have complex configurations with large attack surfaces that make them attractive targets for attackers. So, this type of pen-testing can assist organizations in identifying and fixing vulnerabilities within them.
Network penetration testing is a type of pen-testing that specifically examines networks. Networks connect computers and devices, making them susceptible to eavesdropping, man-in-the-middle attacks, and denial-of-service attacks. Network pen-testing helps organizations quickly detect security flaws within their networks to fix vulnerabilities as soon as possible.
Web application penetration testing (WAP testing) is a branch of pen-testing that specifically tests web applications. These applications provide services to users, including e-commerce, banking, and social media services. Web apps can be vulnerable to numerous attacks, such as SQL injection attacks, cross-site scripting attacks, and denial-of-service attacks. Organizations can quickly identify and address security vulnerabilities within their web apps through WAP penetration testing.
Mobile application penetration testing (MAPT) is a form that examines explicitly mobile applications used on smartphones and tablets. Mobile apps are vulnerable to code injection attacks, data leakage attacks, denial-of-service attacks, and code injection attacks that target code injection vulnerabilities within an application’s code base. These vulnerabilities become security issues and must fix immediately to improve customer experiences and safeguard corporate assets from threats to their mobile applications. PST Teams has expertise in conducting Mobile Application Penetration Tests using tools developed for mobile app testing for Android and iPhone App Development services for organizations.
Types of Penetration Testing Teams
There are two primary categories of penetration testing teams: internal and external.
Internal Penetration Testing Teams
Internal penetration testing teams consist of security professionals employed by the organization. While such teams can provide important insight into its systems and applications, they may need more expertise than external teams.
External Penetration Testing Teams
External teams utilized for penetration testing include security professionals employed by third-party companies. While external teams offer more significant knowledge and experience than their internal counterparts, they may not possess as thorough an understanding of an organization’s systems and applications as their counterparts might.
The appropriate type of pen-testing team for an organization will depend on various considerations, including its size, budget, and security needs.
What Are the Key Penetrating Testing Strategies?
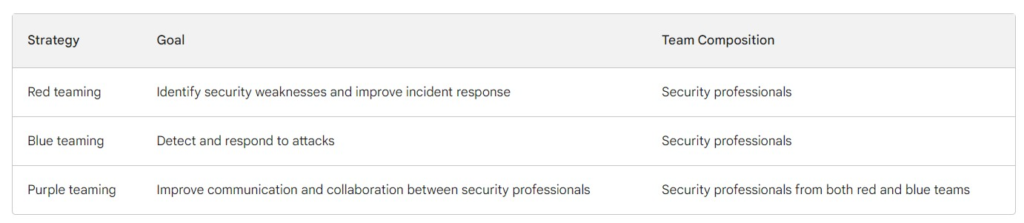
Red, Blue, and Purple Teaming are three security strategies used to increase an organization’s security posture; each has distinct goals and objectives.
Red teaming is a security strategy that simulates an attack by an adversary. This consist of security professionals with expertise in exploiting vulnerabilities within an organization’s systems and networks. The goal is to identify security weaknesses that attackers could exploit and help the organization enhance its incident response plan.
Blue teaming is a security strategy designed to defend against attacks. Blue teams consist of security professionals who monitor an organization’s systems and networks for signs of aggression, aiming to detect and respond swiftly and effectively when threats emerge.
Purple teaming is a strategy that blends the best practices of red and blue teaming to form hybrid security strategies. The aim of this strategy is to increase communication and collaboration among security professionals and create a comprehensive security plan. Purple teams usually include members from both red and blue groups.
Below is a table that highlights some critical distinctions among red teaming, blue teaming, and purple teaming:
Penetration Testing Stages
The steps involved with conducting a penetration test depend upon its type and the needs of an organization. However, here are some general procedures usually adhered to
Planning
The initial step in conducting a penetration test is planning. Therefore this involves testing and identifying all systems and applications, their goals, and establishing realistic timescales.
Discovery
After gathering all information regarding the systems and applications testing, the next step should be collecting more details for testing purposes. Different testing involves this process via a network, social engineering, or vulnerability scanning techniques.
Exploitation
Once teams identify vulnerabilities, they seek to exploit them by trying to gain unauthorized entry, steal information, or disrupt system operations. This may involve trying to gain unapproved access, steal data or cause disruption of the process of systems under testing.
Reporting
Once the penetration test results have been evaluated and reported to an organization, a comprehensive report must include details about any vulnerabilities discovered and recommendations for fixing them.
Benefits of Penetration Testing
Penetration testing can assist organizations in identifying security vulnerabilities that would otherwise go undetected. With this knowledge, organizations can take the steps needed to correct vulnerabilities and enhance system security. Pentesting offers many advantages, such as:
Reducing Risk
Pentesting helps organizations reduce the risk of data breaches or other security incidents by identifying and correcting security vulnerabilities and helping them mitigate them.
Compliance with Regulations
Many regulations, such as Payment Card Industry Data Security Standard (PCI DSS), require organizations to conduct regular pen-testing as part of compliance efforts.
Increased Confidence
Pentesting can help organizations build confidence in the security of their systems. This is especially useful for businesses that deal with sensitive data or are subject to stringent security regulations.
Conclusion
Penetration testing can be invaluable to organizations of all sizes in identifying and remediating security vulnerabilities that attackers could exploit. Furthermore, pen-testing helps organizations improve their overall security posture while decreasing the risk of data breaches. If you want to learn more about pen-testing, there are plenty of resources online; various security firms also offer penetration testing services.

