Achieving the optimal security operations center (SOC) maturity requires a thorough assessment of your cybersecurity posture. The SOC maturity assessment helps you to identify areas for improvement and understand what steps are necessary to realize the most value from your SOC investment.
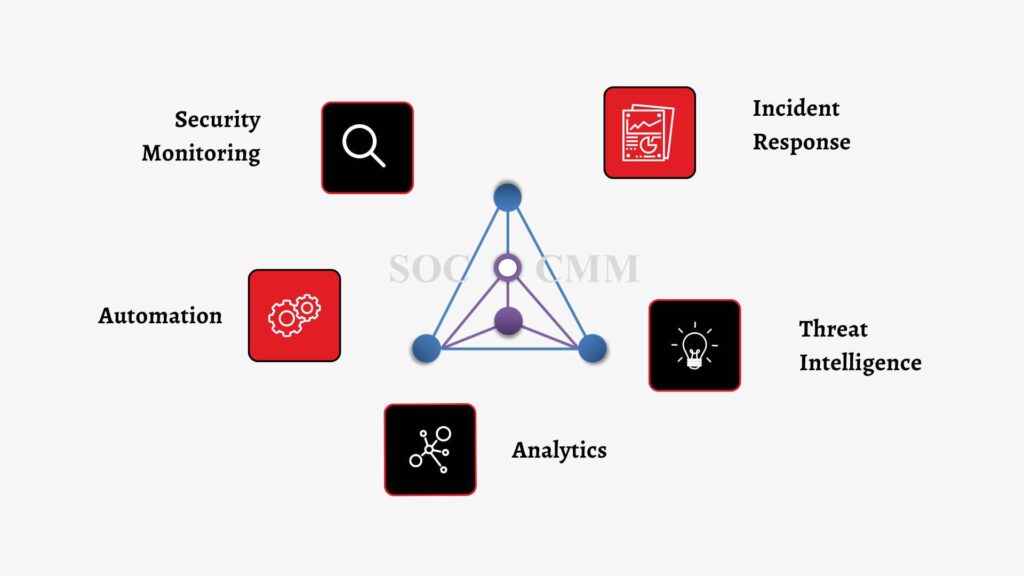
The assessment is divided into five key areas that will help you evaluate the current state of your SOC and identify the necessary steps for improvement:
- Security Monitoring – Understanding what systems, hosts, or networks are monitored by the SOC team and in what capacity.
- Incident Response – Evaluating incident response processes to understand how incidents are investigated and resolved.
- Threat Intelligence – Assessing the threat intelligence capacities of the SOC team and understanding how intelligence is received, analyzed, and acted upon.
- Automation – Understanding the level of automation used by the SOC team and determining what processes could be automated to improve efficiency.
- Analytics – Evaluating the tools being leveraged for analytics as well as whether or not data is being properly utilized for actionable insights.
By leveraging this assessment, you can understand the level of maturity your SOC has achieved and identify what areas need improvement to ensure peak performance.
1: Security Monitoring
The first step in assessing your SOC’s maturity is understanding what systems, networks, or hosts are monitored by the team. This will help determine if any gaps exist that might inhibit the SOC from identifying and responding to threats.
The team should know the answer of the following questions:
- What systems or devices are connected to the network?
- Are these systems monitored for any anomalous behavior?
- Is there a process in place for monitoring user activity on the network?
- Are there tools in place that allow for real-time monitoring of user activity?
- Are there policies and procedures in place to ensure that all systems are monitored consistently?
These questions will help you identify any areas where the security monitoring could be improved. Additionally, it’s also a good practice to evaluate the tools and technology being used for monitoring. Make sure the tools are up-to-date with the latest security requirements and industry best practices.
2: Incident Response
Once monitoring has been established, it’s important to evaluate the incident response processes of your SOC team. This will help you determine whether or not they’re adequately prepared to handle incidents when they arise.
To assess this area, consider the following questions:
- Does the SOC team have a clearly defined incident response plan?
- Are there procedures in place for triaging and responding to incidents?
- Is the team familiar with the incident types they may encounter and how to respond appropriately?
- What tools are being used to analyze and investigate incidents?
- Does the SOC team have access to threat intelligence feeds that can help them better identify and respond to threats?
By understanding the incident response process of your SOC team, you can better assess their capabilities and identify any areas that need improvement.
3: Threat Intelligence
Threat intelligence is an important part of assessing your SOC’s maturity level. Therefore, this will help you understand how the team is able to receive, analyze, and act upon intelligence that can help them identify and mitigate threats.
Consider the following questions to assess this area:
- Does the SOC team have access to threat intelligence feeds?
- Are they receiving timely information from these sources?
- How is the threat intelligence being analyzed for actionable insights?
- Is there a process in place to take action in response to the intelligence?
- Do the team members have adequate training on how to interpret and act upon threat intelligence?
By understanding your SOC team’s threat intelligence capabilities, you can identify any areas for improvement. Additionally, ensure that the team is trained and familiar with the latest security standards and best practices to stay ahead of emerging threats.
4: Automation
Automation is a key component in optimizing the performance of your SOC team. Therefore, by leveraging automated processes, the team can work more efficiently and focus on more complex tasks requiring human expertise.
When assessing this area, consider the following questions:
- Is there an automation process in place for routine tasks?
- Are there tools that can help to automate incident response processes?
- Is the team familiar with the automation processes and how to use them effectively?
- Are there any manual processes that could be automated to reduce workload?
- Does the team have access to support if they need assistance setting up or using the automation tools?
By understanding your SOC team’s automation capabilities, you can identify any areas to improve and ensure that they are leveraging automated processes effectively.
5: Analytics
The final step in assessing your SOC’s maturity level is evaluating its analytics capability. This will help you understand how they leverage data for actionable insights and if any tools or processes are in place to help them do so.
To assess this area, consider the following questions:
- Are there analytics tools being used to detect anomalies or suspicious activity?
- Is the team leveraging machine learning algorithms to build predictive models?
- How is the data being collected and stored for analysis?
- Does the team have access to data visualization tools?
- Is there a process in place for analyzing the data and acting upon it?
By understanding your SOC team’s analytics capabilities, you can identify any areas for improvement. Additionally, ensure they leverage the latest analytics technologies and best practices to gain actionable insights into potential threats.
At the end of the process, you’ll be able to assess how mature your SOC team is and identify any areas for improvement. By leveraging this SOC maturity assessment, you can ensure that your team is properly prepared to handle cyber threats and efficiently monitor and respond to incidents. With proper maturity levels, your SOC will be well-equipped to provide comprehensive security operations excellence.

