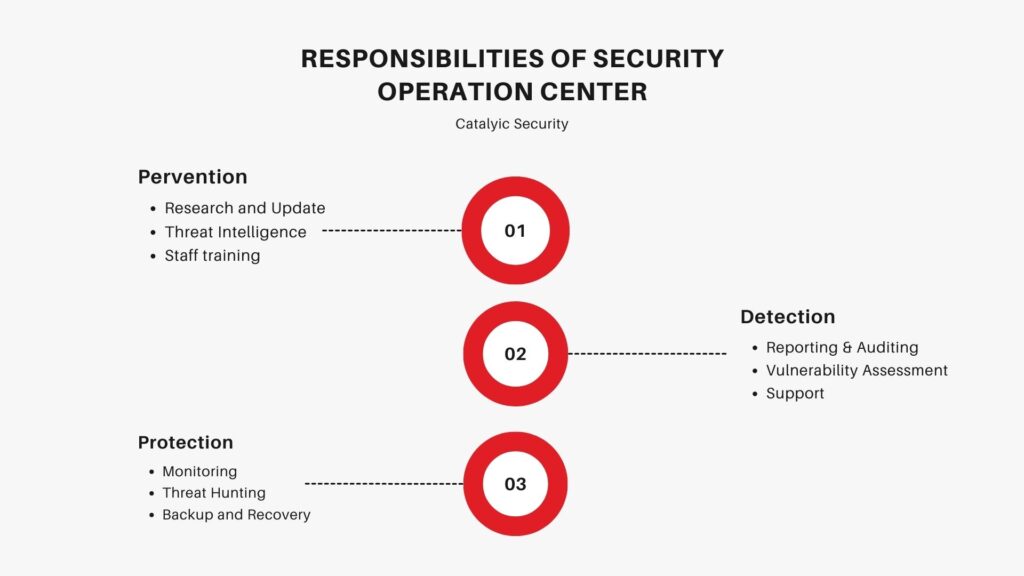
Outsourcing your security operations center (SOC) can be a significant decision for any business. To make the right choice, it’s important to understand all the factors involved in choosing an external provider, such as services offered by SOCs, managed security services providers, and SOC maturity levels.
When looking for a managed security services provider (MSSP) to outsource your SOC, looking for well-established ones with the proper skill set is essential. An experienced MSSP should be able to provide a range of services, including threat intelligence, incident response, vulnerability management, and compliance audits. Additionally, they should have the expertise and resources necessary to properly assess your organization’s security posture and provide recommendations on best practices.
The maturity level of a SOC is also important to consider when making an outsourcing decision. A mature SOC should be able to offer several layers of defense as well as proactive monitoring capabilities. They should also have procedures in place for responding quickly and efficiently to any security incidents that occur.
Difference Between internal SOC and Outsourced SOC
Organizations looking to improve their cybersecurity infrastructure have to decide between developing an internal SOC or outsourcing security operations. While both options can be effective, there are some key differences to consider.
Internal SOC
With an internal SOC, the organization is responsible for recruiting and managing its own team of cybersecurity experts. This includes searching for talent, providing training and education, as well as investing in hardware and software needed for security operations. An internal SOC can also be more expensive and time-consuming to set up, as well as more difficult to scale.
External SOC
Outsourced SOC allows organizations to save on costs and reduce workloads associated with recruiting and managing a team of security experts. Additionally, MSSPs often have the resources and expertise necessary for comprehensive security operations services, making them a more cost-effective way to stay secure.
Ultimately, the decision between developing an internal SOC or outsourcing security operations depends on your organization’s individual needs and budget. It is important to weigh all the pros and cons carefully before making a decision.
Key Considerations for Outsourcing Security Operations
When outsourcing security operations, there are several key considerations to keep in mind.
Cost
The cost of outsourcing security operations is one of the most important considerations. Companies need to evaluate the cost of outsourcing compared to keeping the security operations in-house. Factors to consider include the cost of hiring and training in-house personnel, as well as any additional costs associated with managing an outsourced provider. Additionally, companies should factor in any potential savings that may be realized by outsourcing security operations, such as reduced overhead costs or improved efficiency.
Quality
Another key consideration when outsourcing security operations is quality. Companies need to ensure that they are working with a reputable service provider who can provide high-quality services and solutions. This includes evaluating the provider’s reputation, experience, and customer reviews. Additionally, companies should make sure that the provider has adequate resources and personnel to meet their specific needs and requirements.
Regulatory Compliance
When outsourcing security operations, companies also need to ensure that they remain compliant with applicable laws and regulations. This includes making sure that all data is stored securely and that appropriate access controls are in place to protect sensitive information from unauthorized access or misuse. Additionally, companies should ensure that any third-party service providers adhere to the same standards of privacy and security as required by law or industry regulations.
Service Level Agreements
Finally, it is important for companies to have a clear understanding of the service level agreements (SLAs) associated with their outsourced security operations provider before entering into a contract with them. SLAs outline the terms under which services will be provided by the provider, including response times for requests or incidents, availability guarantees for systems or services, and other performance metrics related to quality assurance or customer satisfaction.
By understanding all the factors involved in choosing an external provider and carefully weighing all pros and cons, organizations can make the right decision when it comes to outsourcing their SOC.
Outsourcing your SOC can be a complex decision, but by understanding all the considerations involved and properly evaluating potential providers, organizations can make an informed decision that is best for their business. It is important to consider factors such as cost, quality, regulatory compliance, and service level agreements when making a decision about outsourcing security operations. With the right provider in place, businesses
FAQ’S
What includes in outsourcing SOC?
Answer: Outsourcing your SOC can include a range of services, including threat intelligence, incident response, vulnerability management, and compliance audits.
What are the benefits of outsourcing SOC?
Answer: Some of the benefits of outsourcing your SOC include cost savings, reduced workloads associated with recruiting and managing a team of security experts, access to expert resources, and improved scalability.
What are the Cons of outsourcing SOC?
Answer: Some of the potential downsides of outsourcing your SOC can include reduced control and oversight, difficulty with ensuring quality service, and compliance risks. Additionally, businesses should ensure that they have a clear understanding of their provider’s terms and conditions to prevent any disputes or disagreements down the line.
How can I evaluate potential providers?
Answer: When evaluating potential providers, organizations should consider factors such as cost, quality, regulatory compliance, and service level agreements. Additionally, businesses should carefully review each provider’s reputation, experience, customer reviews, and resources to make sure they are getting the best possible service. It is also important to ensure that all data is stored securely and that appropriate access controls are in place to protect sensitive information from unauthorized access or misuse.

