Organizations utilize cybersecurity audits as a valuable means to evaluate the efficacy of their existing security measures and uncover any potential vulnerabilities within their IT and OT systems. These audits are important for entities operating critical infrastructure, including power plants, water treatment facilities, and transportation systems, as the ramifications of a cyber-attack on these systems can be highly consequential. By conducting thorough audits, organizations can proactively identify and address any security gaps, ensuring the protection of their critical infrastructure from severe cyber threats.
However, with the increased reliance on computers and technological advancements, attackers have become more sophisticated in their methods. Notably, the industrial sector experienced a significant turning point in 2010 with the emergence of STUXNET, the first high-profile attack specifically targeting industrial control systems (ICS). This event brought global attention to the vulnerabilities in OT networks and marked the beginning of a new era of cyber threats.
Evolution of OT Security
Over the years, the landscape of operational technology (OT) security has undergone significant transformations. Previously, OT heavily relied on computers to monitor and control physical systems, such as SCADA systems managing train traffic on rail networks. In traditional industries, OT security primarily encompassed physical tasks ensuring machines operated flawlessly and assembly lines ran smoothly.
However, with the advent of IT-OT convergence, the perception of OT in factories has shifted, leading to a fundamental change in its security approach. The integration of IT and OT has introduced new complexities and vulnerabilities, necessitating a more comprehensive and robust security framework to safeguard critical industrial processes.
Core Difference between IT and OT
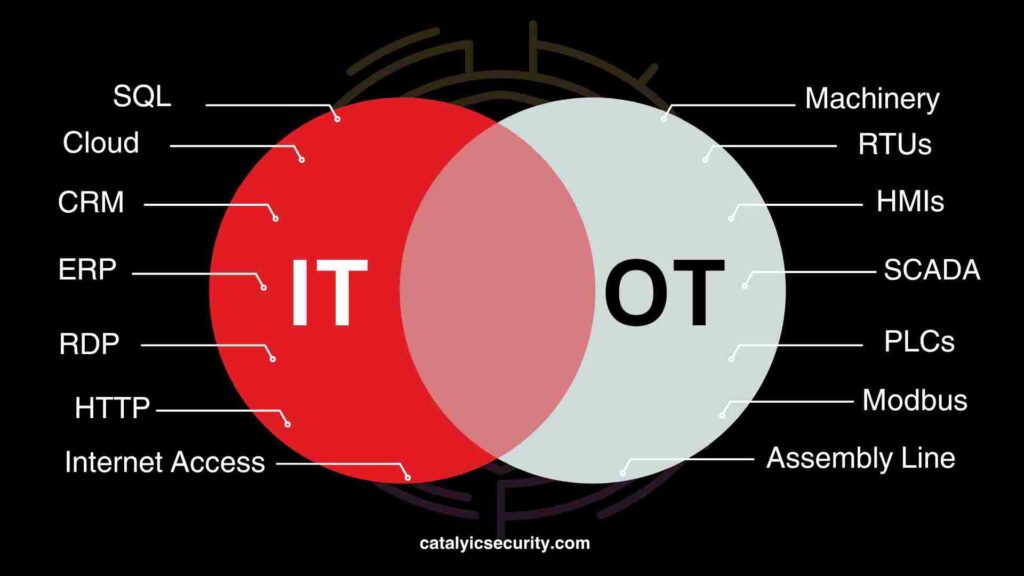
Operational Environment vs. Enterprise Environment:
OT (Operational Technology) and IT (Information Technology) operate in distinct environments. IT primarily deals with digital information, utilizing common technologies and solutions found in enterprise settings. On the other hand, OT operates in industrial environments and involves machinery, PLCs (Programmable Logic Controllers), and industrial protocols specific to physical systems.
Focus on Safety vs. Focus on Confidentiality:
While IT emphasizes the confidentiality, integrity, and availability of data, OT prioritizes the safety and reliability of physical processes and equipment. However, OT systems control critical infrastructure and require meticulous control to prevent accidents or disruptions that could result in financial losses or harm to human life.
Frequency and Magnitude of Incidents:
IT incidents are more frequent due to the larger number of touchpoints with the internet. However, the potential magnitude of OT incidents tends to be more destructive. IT systems have more gateways that can be exploited, whereas compromised OT systems can lead to significant financial losses and widespread ramifications like power outages or water contamination.
Patching and Updates:
IT components undergo frequent updates and security patching to address vulnerabilities. In contrast, patching OT components is challenging because it often requires complete shutdowns, leading to production halts. Consequently, OT components may have more public vulnerabilities and are less frequently updated, increasing the probability of successful exploits.
IT/OT Cybersecurity Audit Process:
Conducting an IT/OT cybersecurity audit involves several key steps to assess the security posture of the combined environment. The following are the typical steps involved in an IT/OT cybersecurity audit:
Scope Definition: Clearly define the scope of the cybersecurity audit, including the specific OT and IT systems, networks, and assets that will be included in the assessment.
Documentation Review: Review relevant documentation, such as cybersecurity policies, procedures, and standards, to understand the existing security framework and controls in place.
Asset Inventory: Create an inventory of all IT and OT assets, including hardware, software, and network components. This helps in identifying which systems need audit and evaluation for security vulnerabilities.
Vulnerability Assessment: Perform a comprehensive vulnerability assessment of the OT and IT systems to identify any known vulnerabilities or weaknesses. This involves using scanning tools, manual assessments, and penetration testing techniques to discover potential security flaws.
Risk Assessment: Conduct a risk assessment to evaluate the potential impact and likelihood of cyber threats affecting the IT/OT environment. Assess the risks associated with critical systems, data, and processes to prioritize remediation efforts.
Compliance Check: Evaluate the organization’s compliance with relevant cybersecurity regulations, standards, and best practices specific to the IT/OT domains. This may include assessing adherence to industry-specific regulations such as NERC CIP or HIPAA.
Security Controls Evaluation: Assess the effectiveness of existing security controls implemented in the IT/OT systems. This involves evaluating the configuration and operation of firewalls, intrusion detection/prevention systems, access controls, encryption mechanisms, and other security measures.
Incident Response Planning: Review the organization’s incident response plan to assess its effectiveness in addressing cybersecurity incidents. Evaluate the procedures for incident reporting, containment, investigation, and recovery.
Security Awareness and Training: Evaluate the organization’s security awareness and training programs for employees, including IT/OT staff. Assess the level of awareness and understanding of cybersecurity risks, policies, and best practices.
Audit Reporting: Prepare a comprehensive audit report that includes findings, vulnerabilities, risks, and recommendations for improving the IT/OT cybersecurity posture. Provide actionable recommendations for remediation, including security control enhancements and policy updates.
Conclusion:
As organizations continue to navigate the digital age and rely on interconnected IT/OT systems, the importance of cybersecurity audits cannot be overstated. The evolution of cybersecurity, especially in the realm of OT security, highlights the critical need for robust protection measures in safeguarding critical infrastructure. The core differences between IT and OT environments necessitate a comprehensive approach that considers the unique challenges and priorities of each. By following a systematic IT/OT cybersecurity audit process, organizations can identify vulnerabilities, assess risks, and implement necessary controls to fortify their security posture. With proactive measures in place, organizations can confidently protect their systems, mitigate cyber threats, and ensure the uninterrupted operation of vital industrial processes.

